Hacking tool : Carry out a MAC spoofing attack
Hacking tool : Learn How to Carry out a MAC spoofing attack
If you would like to prevent an attack of MAC spoofing, you should consider using MAC filtering. This filter is able to make sure that MAC addresses that are not authorized from joining with your wireless network, even if they do happen to have the right password to get into the system.

However, if the hacker is really determined, it is not the most effective way to keep them out, but it can slow them down.
We are going to take some time to learn how to do a spoof of the MAC address of one of the users who is allowed to be on the network. To do this, you have to make sure that the Wi-Fi adapter is going to be placed intomonitoring mode. The tools that are used include Mac changer and Airodump-ng.
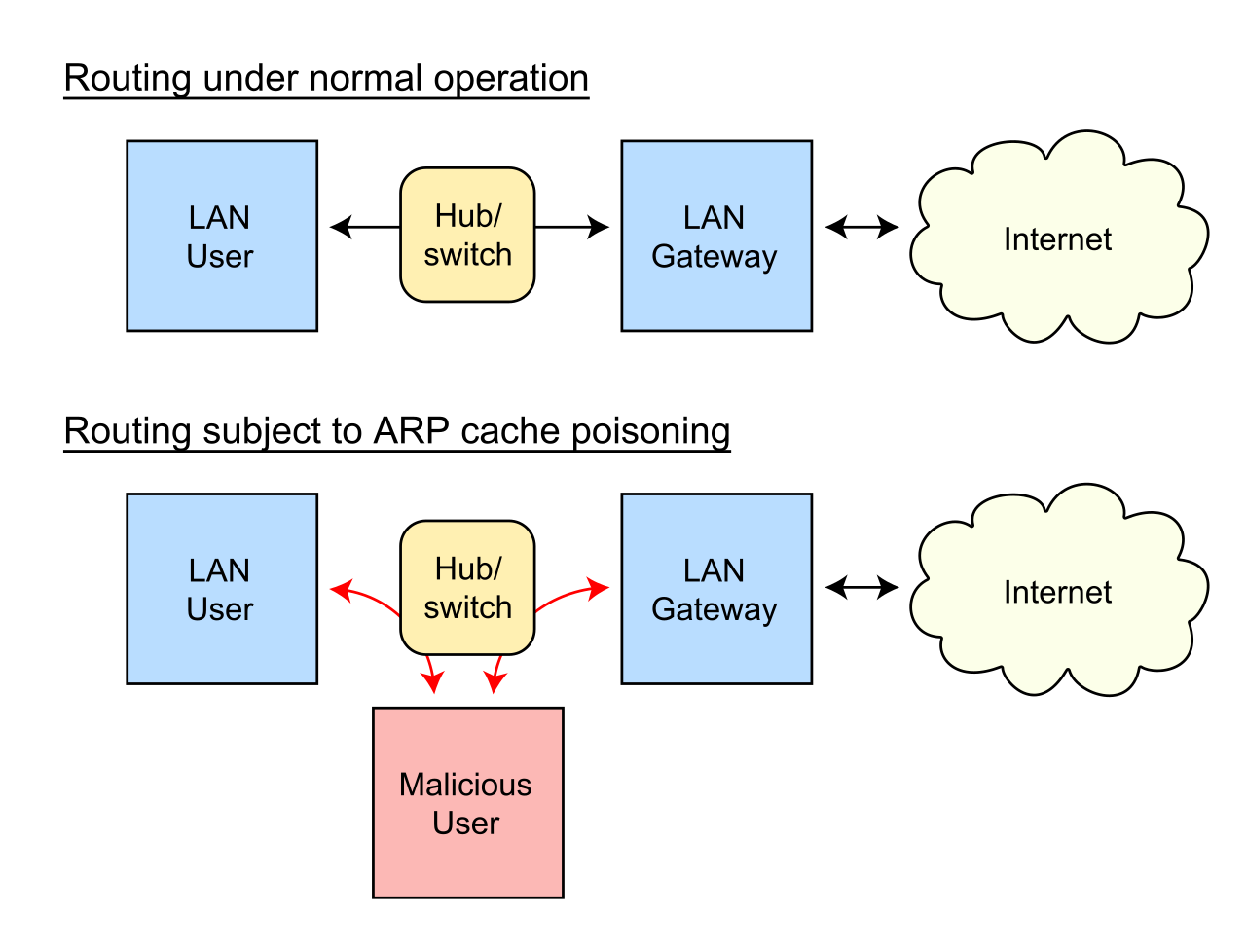
A MAC spoofing attack is where the intruder sniffs the network for valid MAC addresses and attempts to act together of the valid MAC addresses. The intruder then presents itself because the default gateway and copies all of the info forwarded to the default gateway without being detected. This provides the intruder valuable details about applications in use and destination host IP addresses. this permits the spoofed CAM entry on the switch to be overwritten also . this is often best illustrated in Figure 3-9.
Figure 3-9 MAC Spoof Attack
Figure 3-9 MAC Spoof Attack

- MAC C

CAM Table Port 1 Empty Port 2 B Port 3 AC

Step 1 in Figure 3-9 demonstrates the three discovered devices (Devices A, B, and C) within the CAM table. Device C is an intruder. After spoofing the MAC address of Device A (remember, the initial frame when a CAM table is empty is shipped to all or any ports except the source port), Device C sends out a frame with the source address of MAC A, with a replacement spoofed IP address. The switch relearns the MAC address and changes the CAM table entries in Step 2 of the attack. Now when Device B wishes to speak to the legitimate Device A, the switch sends the packet consistent with the CAM table, which is now Port 3 or the attacking PC. Until Device A resends packets, the info flow will remain and therefore the attacker will receive and consider active data. By ensuring that any ARP requests are replied to, the intruder can maintain the connection until manual intervention occurs from the network administrator.
Mitigating this type of attack takes a touch more design because the attacker is way more intelligent. to start out with, you want to enable port security. Example 3-41, earlier within the chapter, displays how this will be achieved.
However, like the CAM table overflow attack mitigation, specifying a MAC address on every port is an unmanageable solution. Another solution would be to use private VLANs to assist mitigate these network attacks.
Using private VLANs may be a common mechanism to limit communications between systems on an equivalent logical IP subnet. this is often not a fool-proof mechanism. Private VLANs work by limiting the ports within a VLAN which will communicate with other ports within the same VLAN.
To configure a personal VLAN on switch-based Cisco IOS or Catalyst OS, follow these steps:
Step 1 Create the primary private VLAN.
Switch_CatOS> (enable) set vlan primary_vlan_id pvlan-type primary name primary_vlan
Switch_IOS(config)#vlan primary_vlan_id
Step 2 Create the isolated VLAN(s).
Switch_CatOS> (enable) set vlan secondary_vlan_id pvlan-type isolated name isolated_pvlan Switch_CatOS> (enable) set pvlan primary_vlan_id secondary_vlan_id
Step 3 Bind the isolated VLAN(s) to the primary VLAN.
Switch_CatOS> (enable) set pvlan primary_vlan_id secondary_vlan_id Switch_IOS(config)#vlan primary_vlan_id
Switch_IOS(config-vlan)#private-vlan association secondary_vlan_id
Switch_IOS(config-vlan)#exit
The best method, in conjunction with port security, is to use DHCP snooping mechanisms to make sure that only valid DHCP servers are enabled across your network. One DHCP snooping mechanism is to allow only trusted DHCP messages to flow between client PC and authorized DHCP servers. the perfect solution to mitigate various ARP-based network exploits is that the use of DHCP snooping along side Dynamic ARP Inspection (DAI).
When a client sends out a broadcast message for an IP address, the intruder's PC also sees the request, of course, because broadcasts are sent bent all interfaces or ports except the source port. So, in effect, the network must not allow DHCP offers, acknowledgements, or negative acknowledgements (DHCPOffer, DHCPAck, or DHCPNak) to be sent from untrusted sources.
Illegal DHCP messages are messages received from outside the network or firewall. The DHCP snooping binding table contains the MAC address, IP address, lease time, binding type, VLAN number, and interface information like the local untrusted interfaces of a switch; it doesn't , however, contain information regarding hosts interconnected with a trusted interface. By configuring trusted and untrusted DHCP sources, the switch are often configured to drop illegal frames immediately. DHCP snooping will still not stop an intruder sniffing for MAC addresses.
DAI determines the validity of an ARP packet supported the valid MAC address—to—IP address bindings stored during a DHCP snooping database. this suggests that only valid MAC addresses are permitted to reply to authorized devices on the network. Some really crafty attackers are out there waiting to pounce on networks, and for a majority of them these features aren't enabled, so it's a gold mine in many parts of the planet even in today's climate.
To enable DHCP snooping, the subsequent commands are required. Example 3-44 enables DHCP snooping. Notice that the sole supported platforms are switches with Cisco IOS-based software.
Example 3-44 Enabling MAC Spoofing on Cisco IOS Switches
!Catalyst IOS switches CatIOS(config)# ip dhcp snooping
CatIOS (config)# ip dhcp snooping vlan number [number] CatIOS (config)# ip dhcp snooping information option ! Enable trusted ports on the DHCP server interface CatIOS (config-if)# ip dhcp snooping trust
The steps that you can use to make this happen include:
- Make sure that the adapter is in a monitoring mode. When the adapter is ready, you will want to type in the following command “Airodump-ng-c [channel]-bssid [target router MAC Address]-I lan0mon”
- This code is going to help you to see the wireless network of the network. All of the users who are able to get into the network will show up on your screen and their corresponding MAC addresses will be there as well.
- You can now pick one of these addresses to use on your computer. You do need to make some changes to your computer, mainly, you need to switch off the monitoring interface. To do this, type in the command “Airmon-ng stop wlan0mon”
- Then you need to switch off the wireless interface of the address that you chose. To do this, you need to type in the command “Ifconfig wlano down”
- Now you need to run the Mac changer software. To do this, you need to type in “Macchanger –m [New MAC Address] wlan0”
- From here, you will need to switch on your wireless interface of the MAC address you chose earlier. You can then type in the command “Ifcofig wlano up”
And now you are all done with doing your work. You have been able to change your MAC address so that it is now the same as one of the authorized users.
If you did this properly, you will be able to log into that particular wireless network and connect to it. If you are successful with getting into the wireless network, you did all of the steps right.