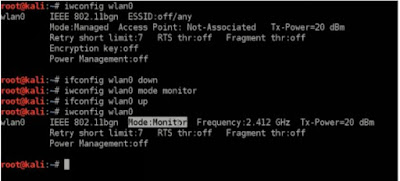
When you want to hack wifi, you need to capture “handshake”. The handshake is connection of personal computer and wireless network, it is when network packet and personal computer packets meet each other. With handshake you do not need to be in wifi range anymore, you can hack password with handshake and wifi name (you will learn this later). Now you need to capture all the packets that are sent through the wifi router and all personal computers in network. There is a question like “if the MAC address is used to ensure that each packet gets delivered to the right place then how we capture it?”, and the answer is that “Yes and no, it is used to send packets to the right destination, and we as hackers can only receive packets that are sent to our MAC address , but this only applies to the default mode of your wireless card, which is ‘managed’ mode, however there is mode that allows us to capture all the packets in our wi-fi range, not only the ones sent to our device, henc...